How to Provide Secure Remote Access to IoT Edge Devices
The following text provides a detailed overview of the concept of secure remote access to IoT edge devices via web, SSH and remote desktop.
- What are the challenges of providing remote access to IoT devices that are behind firewalls and NAT routers?
- What are ‘traditional’ solutions like port forwarding and VPNs?
- How innovative solutions such as macchina.io REMOTE can help you to access IoT devices remotely, without the complexity and security drawbacks of traditional solutions.
- What is Remote Access in IoT?
- How do I Remotely Access an IoT Device?
- How do I Ensure Secure Remote Access for IoT Devices?
- How do I Secure my IoT Connection?
- Why Connecting to IoT Devices Remotely Isn’t so Simple
- macchina.io REMOTE: Best Remote Access Solution
- IoT Device Security
- Best Practices for IoT Security
What is Remote Access in IoT?
Secure remote access is one of the fundamental building blocks of the Internet of Things. Remote access in the context of the Internet of Things (IoT) refers to the ability to access and control an IoT device from a remote computer or device. Several techniques can be employed for this purpose, including Secure Shell (SSH), Virtual Network Connection (VNC), and Remote Desktop Protocol (RDP).
End users want to use a web or mobile apps to access and manage their devices or control their equipment. Service partners need access to devices, installed at remote locations. Support teams need to be able to log-in to devices installed at customer sites.
How do I Remotely Access an IoT Device?
Web interfaces are now standard in IoT edge devices as well as connected embedded systems. They let users configure, control, and monitor hardware via a computer, smartphone, or tablet. Modern web-based user interfaces are powerful, visually attractive and easy to use.
They are perfect for accessing devices remotely, as all that is required is an HTTP(S) connection between the web browser and the device’s web server.
However, for this to work, the web browser on the client PC or mobile device must be able to create a network connection to the IoT device’s web server. This is only possible if the IoT device is located in the same network as the device running the web browser, if the networks containing the client and server are linked, or if the IoT device can be directly reached over the internet.
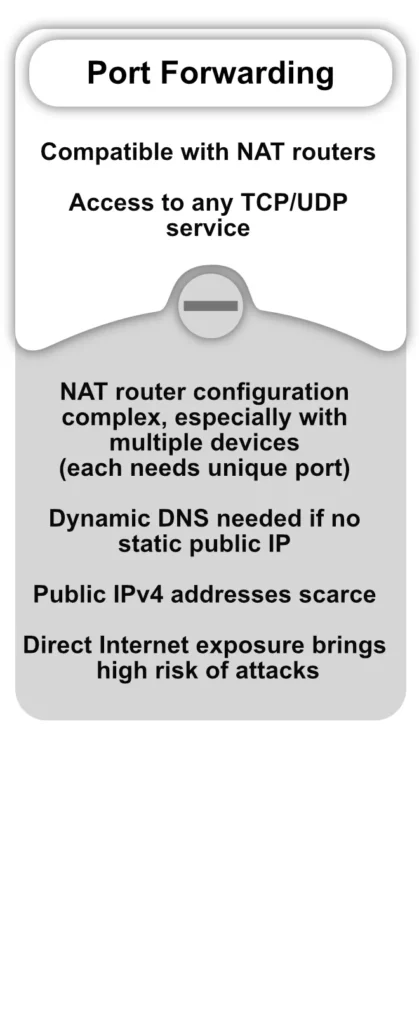
Unfortunately, this is not often the case in reality. NAT (Network Address Translation) routers or firewalls frequently link IoT edge devices in the field to private networks. Industrial IoT devices, usually positioned behind a NAT router, are particularly true examples of this.
Moreover, devices connected to a mobile 4G/LTE network generally lack public IP addresses and are therefore not directly accessible. These devices can connect to the internet, but external sources cannot access them. Not without taking additional measures to enable access to their web server.
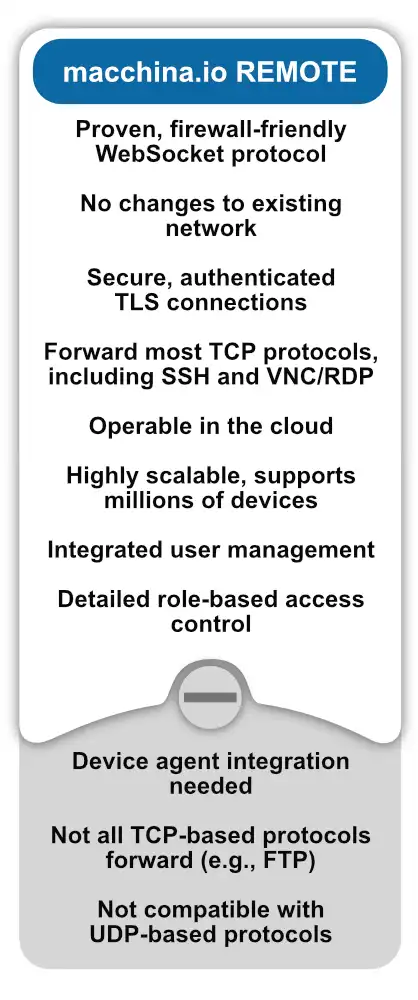
Secure Remote Access with macchina.io REMOTE
macchina.io REMOTE is a great and secure alternative to technologies like NAT port forwarding and virtual private networks. It allows convenient and secure access to IoT devices via web, shell or remote desktop.
The technology can be used without touching the existing network infrastructure. It is suitable for use with end users, service partners or internal support teams.
How do I Ensure Secure Remote Access for IoT Devices?
To ensure secure IoT remote device access:
- All network traffic should use robust encryption such as TLS or DTLS.
- Mandate multi-factor authentication for any administrative access.
- Segregate the IoT network from other networks
- Configure firewalls correctly to allow only the required traffic.
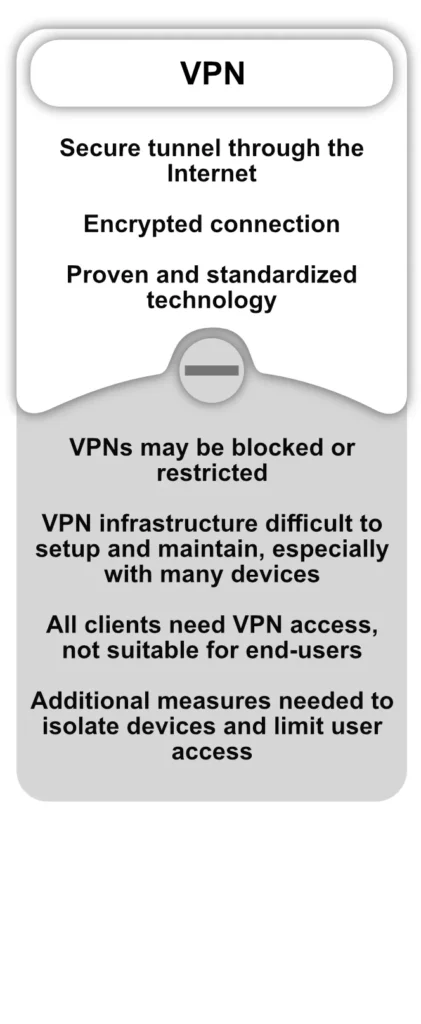
- Use a VPN connection for remote access to the IoT network as necessary.
- Monitor network traffic and devices for any malicious activity.
Port forwarding and VPN allow remote access to computers and network devices behind NAT routers or firewalls. However, these well-known technologies have significant security and complexity issues, particularly when combined with IoT edge devices. For more information, see the table below.
For this reason, Applied Informatics has created a new technology that is a great alternative to port forwarding and VPN: macchina.io REMOTE.
How do I Secure my IoT Connection?
To secure your IoT connection, take these steps:
- Use TLS and HTTPS protocols to encrypt all network traffic between devices and servers.
- Verify identities with API keys or certificates authentication mechanisms.
- Segment the IoT network from other networks using firewalls.
- For any administrative access, require VPN connections.
- Activate the security features of your device including automatic firmware updates, and deactivate unnecessary functions.
- Keep track of network activity on a regular basis to spot anomalies.
What is the Best Way to Secure IoT Devices?
The best way to make sure IoT devices are secure is to build them with security features from the beginning. It is also important to have encrypted communication, access controls, and automatic updates as standard features. Add more layers of security by partitioning the network, mandating multi-factor authentication and supervising traffic.
To ensure security:
- turn off any non-essential features
- utilize safe protocols
- keep firmware up to date
- detect possible threats by using anomaly detection
Implement a layered approach to ensure the security of:
- the equipment
- the network
- access to the equipment.
How does macchina.io REMOTE Enables Web-Based Remote Access to IoT Edge Devices?
macchina.io REMOTE enables easy and secure remote access to an IoT device’s web server and other TCP-based services.
Using our remote access solution you can safely connect to a device on a private or mobile network. Regardless of NAT router or firewall restrictions. You can use either SSH or remote desktop (VNC, RDP) for a secure connection. The following explanation details how this technology works.
Why Connecting to IoT Devices Remotely Isn’t so Simple
Here are some common IoT challenges when implementing remote access to IoT devices:
- Security: Allowing remote access creates potential security vulnerabilities if not properly secured. IoT devices often lack robust security features.
- Connectivity: Device manufacturers deploy many IoT devices in locations with limited internet connectivity. This can make reliable remote access a challenge.
- Scalability: As the number of IoT devices scales to thousands or millions, remote access and management becomes more complex.
- Diversity: Multiple devices and protocols make it difficult to provide a consistent remote access solution.
- Power Consumption: Maintaining a remote connection can drain battery-powered devices.
- Latency: Real-time control is difficult with the latency of Internet connections. Many IoT solutions require local edge computing.
- Cost: Data plans for cellular connected devices can be expensive at scale. Infrastructure costs also increase with large deployments.
- Maintenance: Remote firmware updates and management of disconnected devices adds complexity.
- Monitoring: Monitoring of device health and diagnostic data is essential, but difficult to implement well.
- Compliance: Stringent privacy and security regulations apply to IoT in the healthcare, industrial and other sectors.
Overcoming these challenges requires careful IoT platform design and secure, scalable architectures optimized for remote device access.
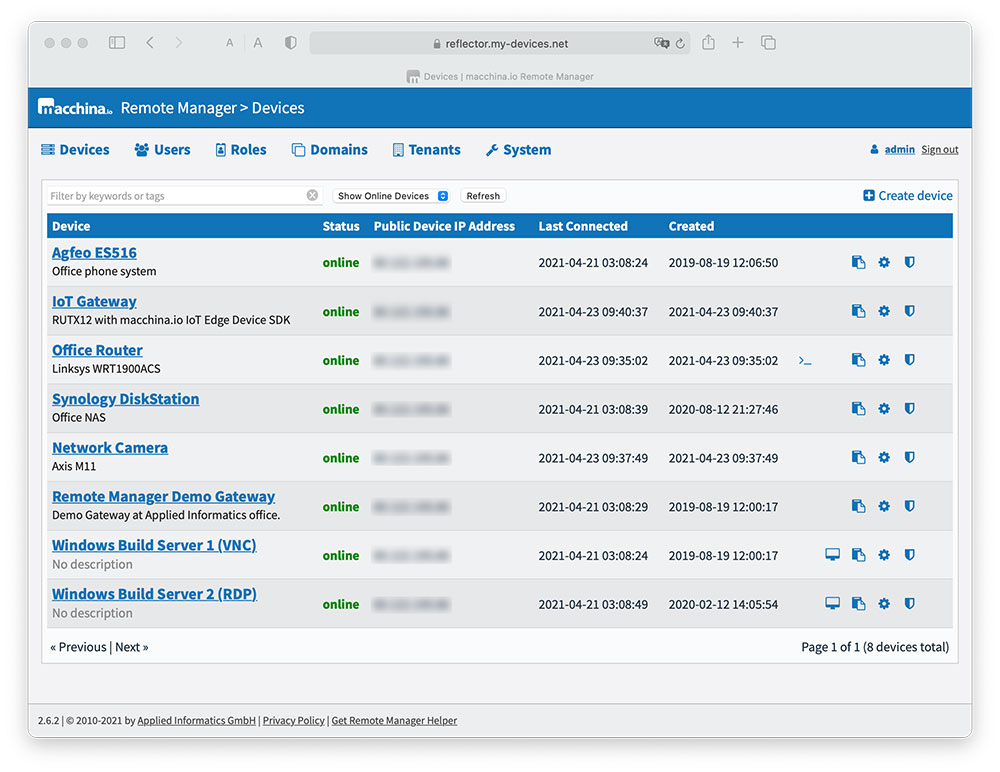
macchina.io REMOTE: Best Remote Access Solution
How Macchina.io REMOTE Works
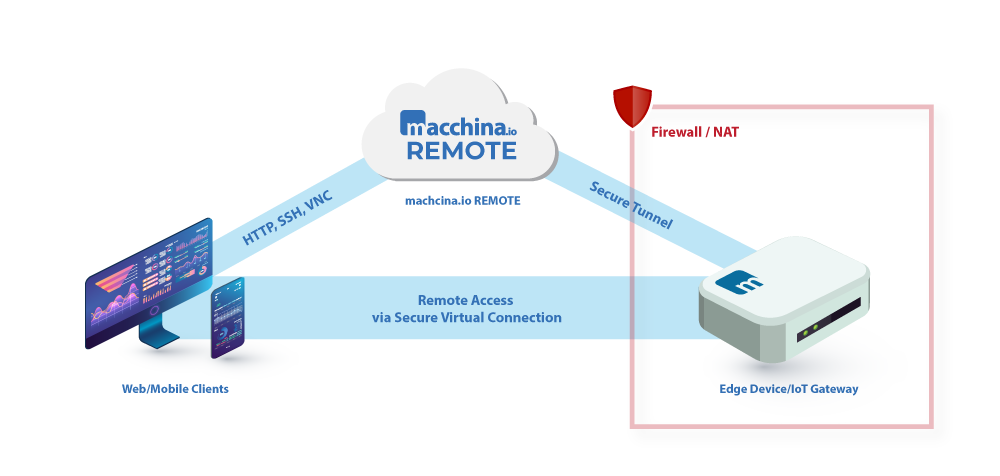
macchina.io REMOTE is based on standard internet technologies, specifically, HTTPS and Web-Sockets. The IoT device needs to run a program called WebTunnelAgent that opens and maintains a secure, TLS-protected and always-on WebSocket connection to the macchina.io REMOTE server running in the cloud.
Once the connection between the device and the macchina.io REMOTE server has been established, the macchina.io REMOTE server uses this connection to send (“tunnel”) HTTP requests and other TCP-based network traffic to the device.
Where do these HTTP requests come from?
The macchina.io REMOTE server also contains a web server, which accepts requests from clients (web browsers). These requests are then simply forwarded to the device, using the device’s tunnel connection.
Setting up the initial tunnel connection between the device and the macchina.io REMOTE server is almost always possible as long as the device can access the Internet. Since the tunnel connection opened by the device uses standard HTTPS and WebSocket protocols, it is very firewall-friendly and even works through an intermediate HTTP proxy server.
Identifying and addressing devices
In a typical usage scenario, users will connect more than one device to a macchina.io REMOTE server. In fact, users could connect tens of thousands of devices to a single server.
Therefore, when the macchina.io REMOTE server receives a HTTP request from a client, it needs to find out to which device the request must be forwarded.
The client sends the URL to the macchina.io REMOTE server (e.g. https://dev1.remote.macchina.io) in the HTTP request to connect to it.
The mechanism relies on a wildcard DNS record in the DNS server which resolves all requests for *.remote.macchina.io to the macchina.io REMOTE server remote.my-devices.net.
The macchina.io REMOTE server can then use the Host header in the HTTP request together with an internal table to associate the request with a device (and its tunnel connection).
Running the macchina.io REMOTE server
There are multiple options for running the macchina.io REMOTE server. The solution can be deployed on an Internet-facing server in a private data centre (on-premises) or on a virtual private server (VPS) provided by a cloud service provider such as Amazon (EC2), Microsoft Azure or Digital Ocean.A dedicated service provider can also run the macchina.io REMOTE server. Multiple macchina.io REMOTE servers can run in a load-balancing setup, making it possible to handle 100.000s or even millions of connected IoT devices.
IoT Device Security
IoT device security requires defense-in-depth protection across devices, networks and back-end systems. A holistic approach to security and threat modeling is essential when implementing IoT systems.
IoT Security Risks
IoT devices face several security issues when deployed. Because IoT devices are interconnected and can access sensitive data, securing them is critical. Some common IoT security challenges include
- Lack of encryption and weak passwords, leaving devices vulnerable to attack. IoT devices often use default passwords that are easy to guess.
- Weak authentication mechanisms that allow unauthorized access. Multi-factor authentication should be used where possible.
- Unpatched firmware and operating systems with known vulnerabilities open devices to exploits. Regular security updates and patches must be applied.
- Insecure network connections, which can allow man-in-the-middle attacks to steal data. IoT traffic should be encrypted using TLS or VPNs.
- Privacy risks from data collection. Data should be anonymised and encrypted to protect user privacy.
- DDoS (distributed denial-of-service) attacks by hijacking multiple devices into botnets. Strong device identification is required.
- Physical tampering of unattended devices to access interfaces. Tamper-proofing such as secure housings can help.
Best Practices for IoT Security
macchina.io REMOTE as an IoT Remote Access Solution
The macchina.io REMOTE server only transparently forwards HTTP requests and TCP connections, but does not store any data passed through it. Exceptions to this are only made for optional caching of images and style sheets in order to improve performance over low bandwidth network connections.
Therefore the macchina.io REMOTE server does not introduce any additional data security and privacy risks, reducing security concerns and potential issues. This also holds true if the macchina.io REMOTE server is operated in a private data center.
Both the connection between the device and the macchina.io REMOTE server, as well as the connection between the client (web browser) and the macchina.io REMOTE server are encrypted and secured with state-of-the-art TLS.
This technology is inherently secure. Furthermore the device does not need to have any open ports to the Internet so there is no danger of denial-of-service or other kinds of attacks against the device.
Additional Security and Privacy Features of macchina.io REMOTE
- requests to the device can only be sent through the macchina.io REMOTE server,
- the macchina.io REMOTE server requires proper authentication of the user before forwarding requests to the device,
- devices must authenticate themselves against the macchina.io REMOTE server when setting up the tunnel connection,
- device authentication is done through a shared secret or certificate.
User Accounts, Roles and Permissions
The macchina.io REMOTE server supports user account management features and role- and permission-based access control, making it easy to specify which users may access and manage which devices.
Works for Web, SSH and Remote Desktop
macchina.io REMOTE is not just for accessing web pages. Virtually every TCP-based protocol can also be used over a macchina.io REMOTE tunnel connection, including web services based on REST, JSON-RPC or SOAP technologies, or secure shell (SSH) and remote desktop (VNC, RDP) protocols.
macchina.io REMOTE even includes a web-based VNC client. This makes it a great foundation for automated device management applications and remote support/maintenance portals.
Easy Integration and Customised Deployment
The software necessary for integrating macchina.io REMOTE into a device, as well as the macchina.io REMOTE server is provided by Applied Informatics.
For devices where the necessary modification of the firmware is not possible or feasible, a low-cost gateway device can be used to connect the device to the macchina.io REMOTE server.
The gateway is located in the same local area network as the device, and forwards requests from the macchina.io REMOTE server to the device’s web server.
It’s also possible to install the gateway software on a mobile internet router. The macchina.io REMOTE server can be integrated with other applications via its REST API.
The default web user interface of the macchina.io REMOTE server can be customized to match customer-specific needs and visual style.
The macchina.io REMOTE server optionally supports LDAP for user authentication.
Secure Remote Access Made Easy
macchina.io REMOTE is a powerful and secure option, better than NAT port forwarding and virtual private networks. It allows access to IoT devices via web, shell, or remote desktop in a smooth and safe way. Also, it can be used on existing network infrastructure, so it’s perfect for end users, service partners, and internal support teams.

The necessary macchina.io REMOTE server can be operated in “the cloud”, and devices can be easily integrated, either by updating their firmware or by using a special gateway device or 4G/LTE router.
macchina.io REMOTE can be used for free with up to five devices. For more information as well as tips for getting started, please visit the website at https://macchina.io.